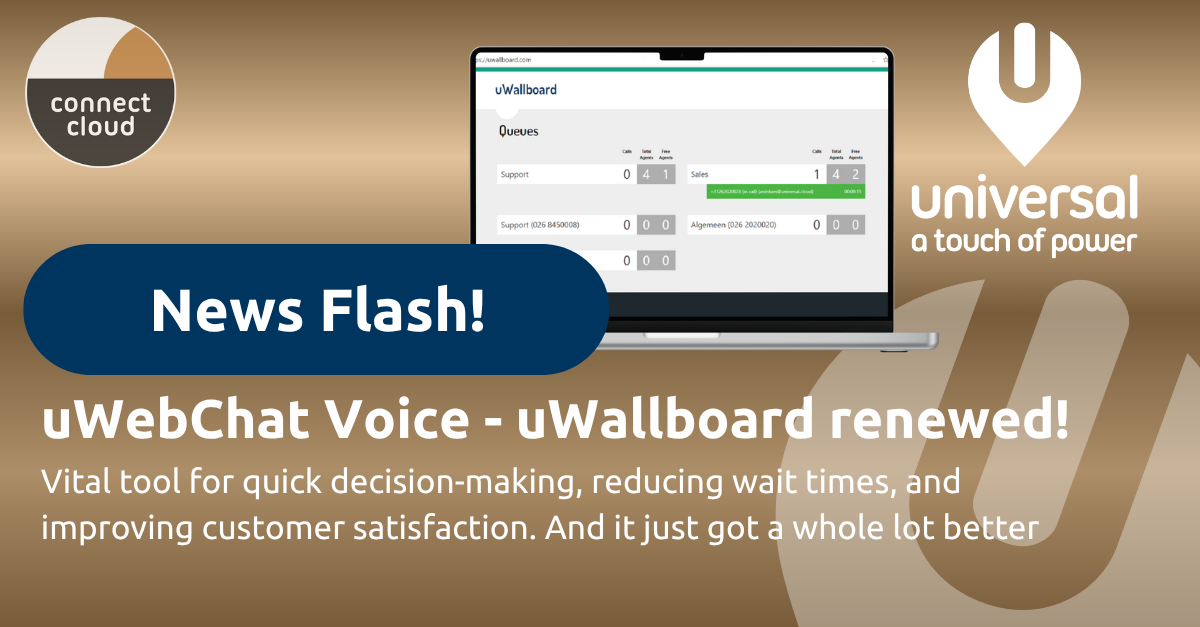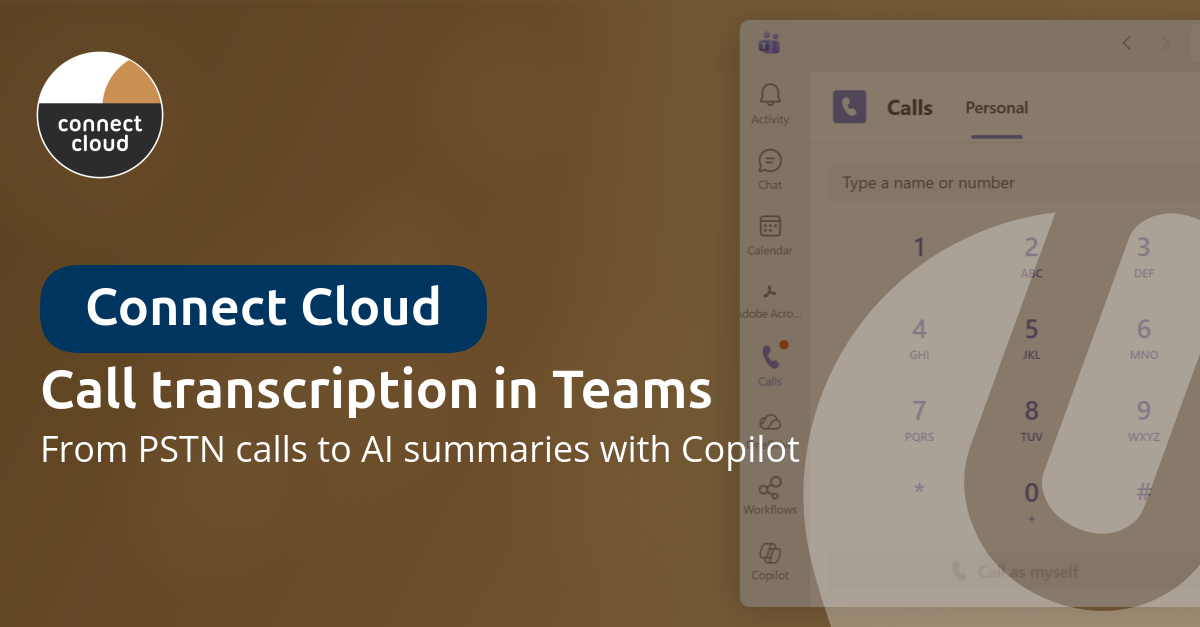
Call transcription in Teams: turn every phone call into an actionable summary
Discover how to automatically transcribe PSTN calls in Microsoft Teams, which license you need, and how Copilot turns every conversation into an actionable summary.
Read More